Ensuring Robust Security Measures for Financial Services and Web3 Environments in 2026
Last updated: Feb 21, 2026
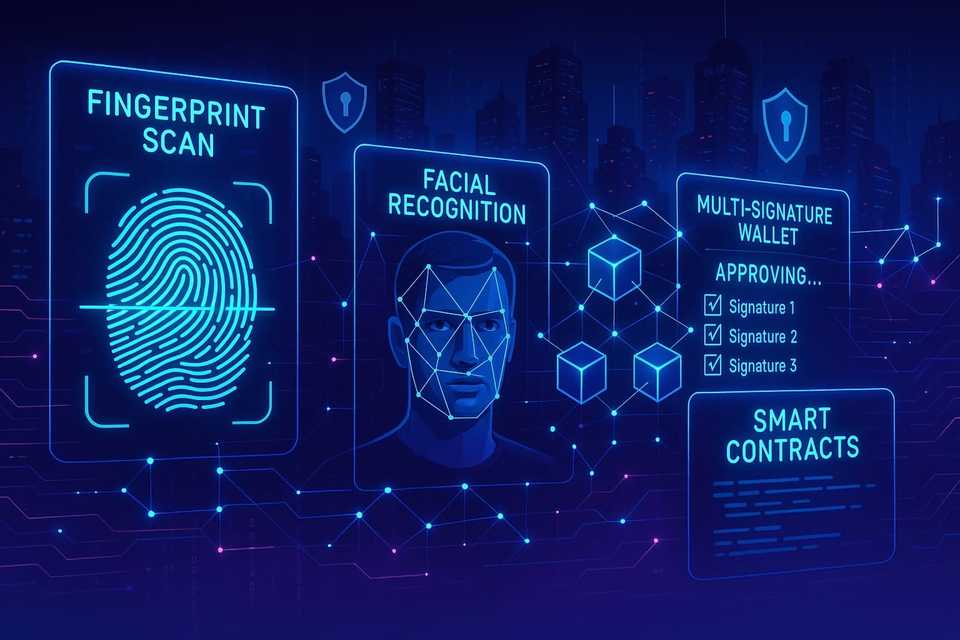
Implement multi-layer authentication procedures across your platform to ensure that every user is thoroughly verified. Consider deploying biometric verification alongside traditional methods, as this significantly reduces the risk of unauthorized access.
Employ regular vulnerability assessments to identify any potential weaknesses in your system. Utilizing automated tools can streamline this process, allowing for continuous monitoring and rapid response to emerging threats.
Incorporate advanced encryption techniques for data transmission and storage. Utilize end-to-end encryption protocols to safeguard user information from interception during transactions, reducing exposure to data breaches.
Establish a dedicated incident response team tasked with managing any security breaches. Regularly conduct simulations to prepare your team for real-world scenarios, ensuring swift and effective reactions to potential threats.
Leverage decentralized identity solutions to empower users. By allowing individuals to control their personal data and only share it when absolutely necessary, you minimize the risk of mass data exposure. Integrating defi security services into your architecture further strengthens protection against protocol-specific vulnerabilities.
Invest in continuous staff training programs focusing on cybersecurity awareness. Human error often serves as the weakest link, so informing your employees about phishing attacks and other common threats can enhance your platform’s defenses.
Implementing Decentralized Identity Solutions for User Authentication
Utilize blockchain-based decentralized identity frameworks, such as self-sovereign identity (SSI) models. These solutions empower users with control over their personal data, reducing the risk of unauthorized access. Implement protocols like Verifiable Credentials (VC) to authenticate users without exposing sensitive information, enhancing privacy.
Integration of Biometric Technologies
Incorporate biometric verification methods alongside decentralized identities. Fingerprint or facial recognition systems can serve as an additional authentication layer, ensuring that access to services is limited to authorized individuals. Consider using secure biometric data storage options to maintain user confidentiality while allowing rapid verification.
Utilization of Multi-Factor Authentication
Combine decentralized identity systems with multi-factor authentication (MFA) techniques. This could involve confirming user identity through combinations of something the user knows (password), something the user has (digital wallet), and something the user is (biometric data). This multi-layered approach significantly mitigates risks associated with identity theft.
Engage in continuous monitoring and updating of authentication protocols to adapt to emerging threats while maintaining user convenience. Regular audits of the identity verification process can ensure compliance with evolving regulations and best practices. Encourage users to participate in their identity management, making them aware of potential phishing attacks and promoting secure practices.
Utilizing Smart Contracts for Automated Risk Management
Implement smart contracts to automate compliance checks and dynamically assess risk factors. By setting predetermined conditions within the code, these contracts can execute trades or transactions only when specific risk thresholds are met, ensuring real-time control over potential exposures.
Deploy oracles to feed external data into smart contracts, allowing for accurate and timely risk assessment based on market fluctuations. Utilize this data to activate risk mitigation protocols without manual intervention, significantly reducing response times and human error.
Incorporate multi-signature functionality to enhance the governance of smart contracts. This will require approval from multiple stakeholders for executing transactions, thereby adding an extra layer of verification and reducing fraud likelihood.
Regularly audit smart contracts to identify vulnerabilities and ensure code integrity. Use formal verification methods to mathematically prove that the contract behaviors align with risk management protocols, minimizing exposure to known exploits.
Employ machine learning algorithms in conjunction with smart contracts to predict and react to market risks. By continuously analyzing transaction data, these algorithms can adjust smart contract parameters, improving performance and resilience against volatility.
Leverage insurance mechanisms within contracts to provide coverage in case of breaches or unexpected losses. Automated claims processing can simplify recovery efforts, allowing affected parties to receive compensation without lengthy negotiations.
Integrating Multi-Signature Wallets for Enhanced Fund Security
Implement multi-signature wallets where multiple private keys are required to authorize a transaction. This setup significantly reduces the risk of unauthorized access since no single individual can manage funds alone. Allocate separate keys among trusted team members or stakeholders, ensuring that consensus is met before any action is taken.
Key Components of Multi-Signature Wallets
Select the appropriate signing mechanism. Common configurations include 2-of-3 or 3-of-5, where a minimum number of keys must sign off for a transaction to proceed. Ensure all participants are well-informed about their responsibilities and access protocols to maintain accountability.
Utilize wallets with clear user interfaces to minimize errors during transactions. Adopting tools with audit trails can enhance transparency, allowing for easy tracking and verification of fund movements.
Integrating with Existing Infrastructure
Incorporate these wallets into current platforms seamlessly. Review application programming interfaces (APIs) and ensure compatibility with existing financial systems. This will facilitate straightforward integration and reduce operational hurdles during implementation.
Engage in rigorous testing before full deployment. Simulate various scenarios to identify potential vulnerabilities in multi-signature workflows. Educate all users on best practices for managing their keys and using the wallet efficiently.